A new script has been shared for capturing a native Microsoft etl network trace on a Windows machine without the need for 3rd party tools like Wireshark. This can be used within ControlUp Real-Time and allows for simultaneous tracing on multiple machines. Bonus: process ids are available for every packet and filters can be applied with Wireshark. Code snippet provided.
Read the entire ‘ControlUp’s Native Microsoft ETL Network Trace Script’ thread below:
Here’s a new script that will capture a native Microsoft etl network trace on a Windows machine (so no 3rd party tools like Wireshark are required to capture the trace and no drivers loaded). The only required parameter is the duration, in seconds, which defaults to 30.It downloads a signed utility from Microsoft on GitHub (https://github.com/microsoft/etl2pcapng) and runs it on the trace to produce a (pcapng) file that Wireshark, running anywhere and it doesn’t have to be elevated, can read and display.
Use it within ControlUp Real-Time and you can launch it on 2 (or more) machines simultaneously, for instance to capture a trace at both ends of something you are troubleshooting.
A bonus with capturing packets natively with Microsoft technology is that the process id (PID) for every packet is available and can be filtered on in Wireshark!
Filters can be applied in the capturing or use Wireshark’s extensive range.
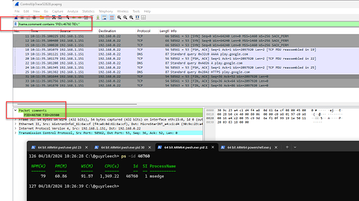
This looks very interesting. Wireshark is able to read the ETL files without converting them as well, just have to load them properly. I have a little snippet of code that I have been using to start and stop traces for various little troubleshooting tasks. It’s pretty handy to be able to start the trace, run a command in PowerShell and stop the trace all in the same script so the capture is pretty focused on the task at hand.
Continue reading and comment on the thread ‘ControlUp’s Native Microsoft ETL Network Trace Script’. Not a member? Join Here!
Categories: All Archives, ControlUp Scripts & Triggers
