A discussion about a new GPO led to the suggestion of creating a report on devices that have received the GPO using ControlUp and scraping the output of the gpresult command. Information on how to do this can be found in a recent ControlUp blog post. A script was also provided for converting the output to json and generating a report. A link to the post and the script was included.
Read the entire ‘Generating Reports on GPO Application with ControlUp’ thread below:
Hi, I have implemented a new GPO for the devices. Since there is no telling from the GPO which device has gotten the GPO, I wanted to know if there is a way with ControlUp to have a report of the devices that have got the GPO applied or if a registry search could be done.
This is a great idea. I don’t think it’s something we can do out of the box, but it sounds relatively easy to script
You should be able to run gpresult and scrape the output and put it into a custom index. Just requires a bit of scripting.
Beat ya
lol
@member Great idea here.
@member do we have something in the works for this
Darn
Beat ya
I had it ready but noticed that I tagged the wrong bill powell account
"Just requires a bit of scripting." – who said that?
I’m adding it to the Monday board right now.
We already have this https://www.controlup.com/script-library-posts/list-user-gpos/
Just need to make it work for Edge
(I said that btw)
So just needs conversion to EdgeDX – which should be straightforward.
@member – you used the ‘easy’ word, too.
thanks for the fast response!
Is it possible to do it on the computer side not user?
gpresult /r /scope computer. Yep.
@member I’ve noted that preference.
In the meantime you can run the GPResult command one off or on multiple machines and just send the output to an event. Add a new Powershell script, click the Add "Send Events" link and put this one line in the output block.
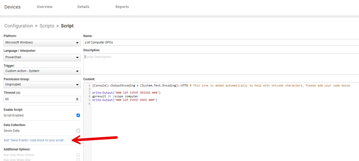

then a report can be generated from this?
No report. It just creates an event with the data in the machines Device Events. Its one-off.
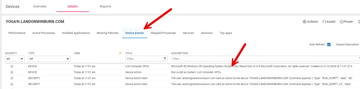
got it
Im looking for a way to confirm a device received a specific GPO
then get a report
Yep, this would work for a one-off verification. A report would need the "Sends data" and a custom index. The output would need to be scraped to get the policies and then converted to json.
https://www.controlup.com/resources/blog/entry/automatically-collecting-information-on-your-users-monitors-model-and-date-of-manufacture/ good recent post on how to put things in an index and create a report
you can query the event log for the gpupdate occuring and go by the date time stamp. We have done this on occasion with the Applocker GPO.
Something like this? (Tested on a domain-joined device, but I don’t have EdgeDX installed – @member can you check this out?)
“`#
script to parse gpresult
$script:now = Get-Date
$script:ComputerName = $env:COMPUTERNAME
[datetime]$script:WMILastBootTime = (Get-CimInstance -ClassName Win32_OperatingSystem | Select-Object LastBootUpTime).LastBootUpTime
[datetime]$script:PoliciesAppliedDate = $script:WMILastBootTime.AddDays(-1)
$computerInfo = Get-CimInstance -ClassName Win32_ComputerSystem
if (-not $computerInfo.PartOfDomain) {
Write-Host -ForegroundColor Yellow "$env:COMPUTERNAME is not part of a domain"
exit 0
}
function New-Policy {
[CmdletBinding()]
param (
[parameter(mandatory = $true)][string]$PolicyName,
[parameter(mandatory = $true)][string]$Action,
[parameter(mandatory = $false)][string]$Notes
)
if ($script:PoliciesAppliedDate -lt $script:WMILastBootTime) {
$PolicyTime = ‘N/A’
}
else {
$PolicyTime = $script:PoliciesAppliedDate.ToString(‘O’)
}
[pscustomobject]@{
Policy = $PolicyName
Action = $Action
Notes = $Notes
PolicyTime = $PolicyTime
PolicySource = $script:PolicySource
BootTime = $script:WMILastBootTime.ToString(‘O’)
ComputerName = $script:ComputerName
ComputerDomain = $computerInfo.Domain
ComputerDN = $script:ComputerDN
}
}
$State = ‘Skipping’
$GPOutput = gpresult /r /scope computer
$PolicyRec = $null
$recordQueue = New-Object System.Collections.Queue
$GPOutput | Where-Object {$_ -notmatch "^\s-+\s$"} | ForEach-Object {
$Line = $_
if ($Line -match "^\sThe computer is a part of the following security groups\s$") {
$State = ‘Skipping’
}
elseif ($Line -match "^\s(?<cdn>CN=.DC=\S+)\s*$") {
$script:ComputerDN = $Matches.cdn
}
elseif ($Line -match "^\s(?<pre>\S.?\S):\s+(?<post>\S.?\S)\s$") {
if ($Matches.pre -eq "Last time Group Policy was applied") {
$AppliedTime = $[Matches.post](http://Matches.post) -replace " at ",’ ‘
$script:PoliciesAppliedDate = [datetime]::Parse($AppliedTime)
}
elseif ($Matches.pre -eq "Group Policy was applied from") {
$script:PolicySource = $[Matches.post](http://Matches.post)
}
}
switch ($State) {
‘PoliciesApplied’ {
$PolicyText = $Line -replace "^\s+|\s+$",”
if ([string]::IsNullOrWhiteSpace($PolicyText)) {
$State = ‘Skipping’
$PolicyRec = $null
}
else {
$PolicyRec = New-Policy -PolicyName $PolicyText -Action ‘Applied’
$recordQueue.Enqueue($PolicyRec)
}
}
‘PoliciesSkipped’ {
$PolicyText = $Line -replace "^\s+|\s+$",”
if ([string]::IsNullOrWhiteSpace($PolicyText)) {
$PolicyRec = $null
}
else {
if ($PolicyRec -eq $null) {
$PolicyRec = New-Policy -PolicyName $PolicyText -Action ‘Skipped’
$recordQueue.Enqueue($PolicyRec)
}
else {
$PolicyRec.Notes = $PolicyText
}
}
}
default {}
}
if ($Line -match "^\sApplied Group Policy Objects\s$") {
$State = ‘PoliciesApplied’
}
elseif ($Line -match "^\sThe following GPOs were not applied because they were filtered out\s$") {
$State = ‘PoliciesSkipped’
}
elseif ($Line -match "^\sRSOP data for (.) on (?<computer>\S(.\S){0,1}) : (\S(.\S){0,1})\s*$") {
$State = ‘StaticData’
$script:ComputerName = $Matches.computer
}
# Write-Host -ForegroundColor Cyan $Line
}
Write-Output ("### SIP DATA BEGINS ###")
$recordQueue | ConvertTo-Json
Write-Output ("### SIP DATA ENDS ###")“`
Notes:
This is proof-of-concept, so any feedback on which fields I’ve omitted or which fields are superfluous would be welcome.
Dates are rendered as ISO 8601 compatible, rather than local format
Policy updates are disregarded if they precede the last boot time, so what goes in the index represents current state.
Yep, confirmed working. Thank Bill!
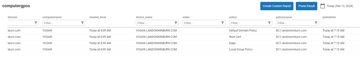
And thank you. I’ll get that added to this month’s EdgeDX release.
Continue reading and comment on the thread ‘Generating Reports on GPO Application with ControlUp’. Not a member? Join Here!
Categories: All Archives, ControlUp for Desktops, ControlUp Scripts & Triggers
